Cybersecurity Part 1: The threat of threat analysis

We start 2024 with a new series of cybersecurity blogs. In this first part we look at pragmatic approaches to threat analysis. As most industries are nowadays very much focused on cybersecurity, we are all faced with the challenges of defining what an acceptable cybersecurity residual risk is. Nothing different there to other technical areas, we require a strategy for hardware, software, and usability, that have varying input criteria and output acceptance. For cybersecurity there are numerous sources of information defined in reference material and international standards as we covered in our blog IEC 62304 – Part 4: Cybersecurity opening the flood gates. How do you approach the topic of a pragmatic strategy for defining an acceptable cybersecurity risk?
The center piece of cybersecurity threat strategies in both automotive (ISO SAE 21434) and the medical device industry (AAMI TIR 57), is the National Institute of Standards and Technology (NIST) SP 800-30. The approach is best illustrated diagrammatically from AAMI TIR 57.
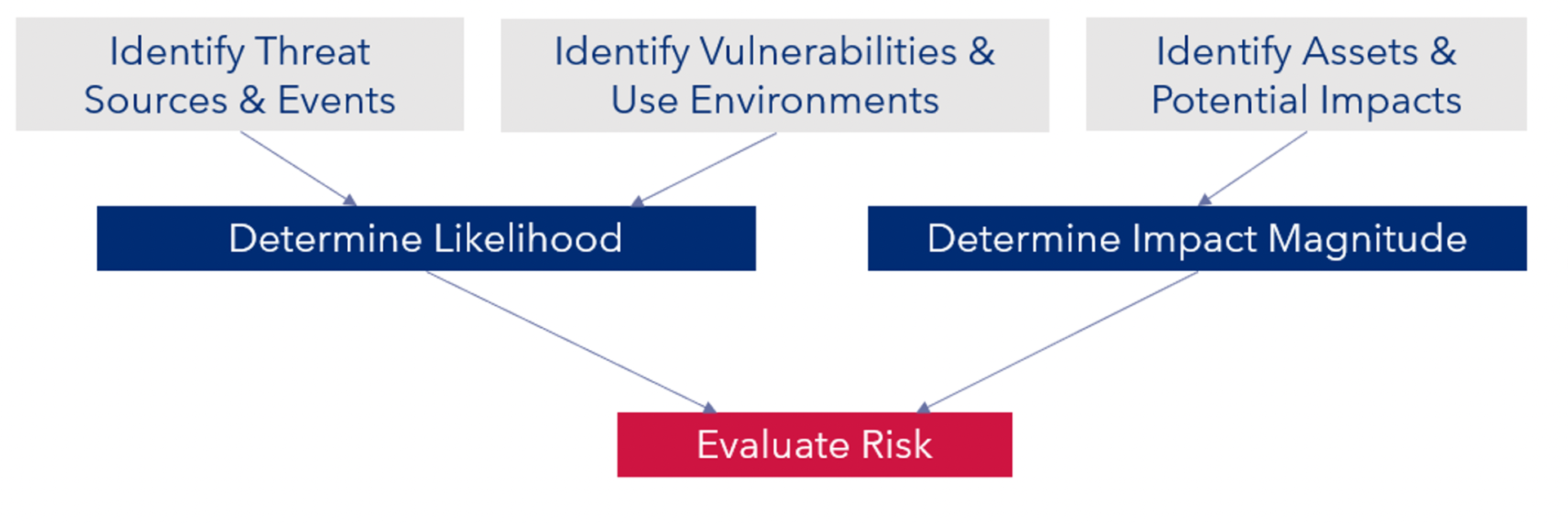
The process generating a likelihood and impact level for threats, the combination of which yielding a risk outcome. ISO SAE 21434, taking a similar approach.
The factors that feed into this risk outcome are, however, sub-divided into many categories. In NIST SP 800-30, there are two key routes to reach the final risk score, based on adversarial or non-adversarial threats, the former having the greater number of factors. In figure 2 we have listed the 13 categories each having its own column and the qualitative risk level scale (a semi-quantitative scoring system is also defined in the document).
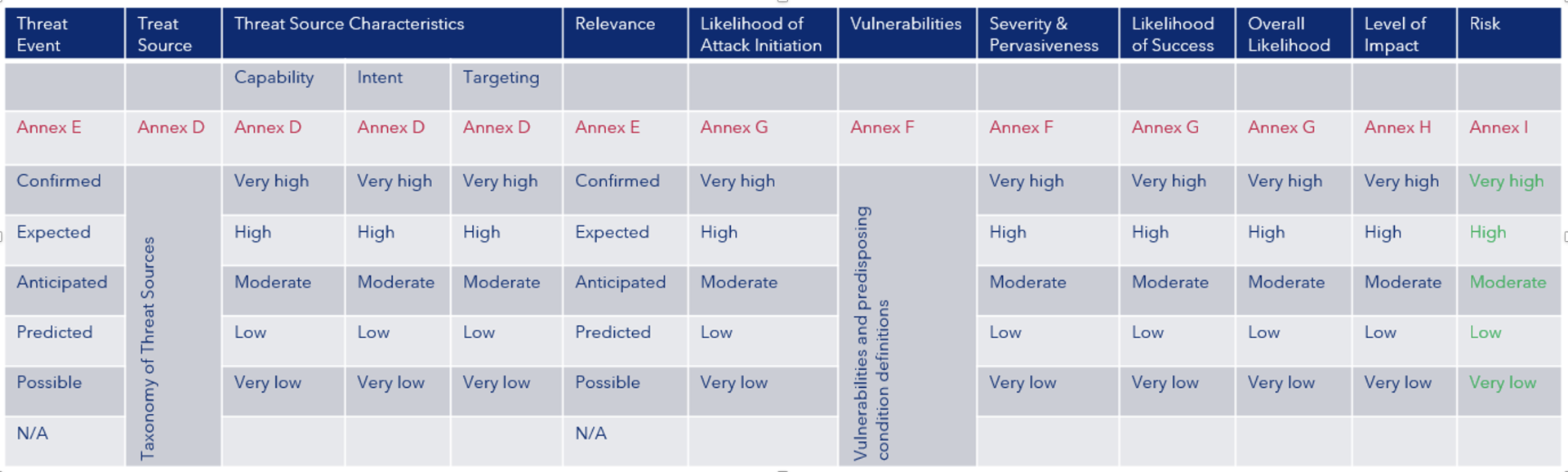
Some customers use this approach to define the risk score as illustrated in green in the right-hand column, but for adversarial with 10 columns contributing to the overall risk level, each with 5 or 6 potential ratings, this leads to a very complex assessment of cybersecurity risk acceptance. Where weighting of the result is required, based on specific input criteria is one of the challenges. However, it brings flexibility in the process that does not necessarily come from more pragmatic approaches.
The NIST series of standards brings many practical tips and guidance in all sorts of technological areas, hence an invaluable reference source.
With the release of version 4.0 of the Common Vulnerability Scoring System (CVSS) last year, we have an updated version of a well tried and tested open framework tool. Using such a tool certainly makes life easier for those defining the cybersecurity risk strategy and ultimately the acceptable residual risk. There has been criticism of the CVSS metrics over the years around suitability to address modern industry challenges, but V4.0 has improved many aspects of the scoring system.
The main advantage to using such a tool, and there are many others such as Common Weakness Enumeration (CWE), is that a scoring system and acceptance threshold does not need to be devised. The tools are readily available online and hence save a significant amount of effort when generating a cybersecurity risk management plan, as the tool defines the acceptance level.
That CVSS is used globally by a huge number of organizations and is extremely useful in providing a standardized approach to analyzing threats.

Take a closer look at cybersecurity risk assessment strategies in our Automotive Cybersecurity or Medical Device Cybersecurity course. Schedule your next training with us or send a direct inquiry at info@lorit-consultancy.com.
Erfahre mehrOne key aspect with a threat analysis is that the activity does not end at product release and continues throughout the expected service life of the product. Regardless of the strategy an approach should be used that enables teams or individuals to quickly reassess new vulnerabilities identified e.g. in Software of Unknown Provenance (SOUP) as it is referred to in the medical device sector or Commercial of the Shelf Software (COTS) in other industries. One area still that is finding its feet in many organizations is the post-market cybersecurity process. An individual maybe assigned the task of monitoring the cybersecurity landscape and identifying new vulnerabilities. These then being quickly assessed for their risk score and hence the decision on the next course of action. CVSS or similar tools lend themselves well to support this process stage.
Ultimately how teams approach that analysis should be down to the industry and technology used with a key focus on the assets in the product. Developing risk management strategies in any industry can be challenging and it should ensure that in the world of cybersecurity threats shall not be missed but at the same time the process is not overly complex. Well-established tools such as CVSS help in this respect as they reduce the burden of defining acceptability. This thought should be balanced up with the flexibility of the tool as it may not always tick the boxes for your given approach, hence where the NIST SP 800-30 strategy may come in handy.
In our next blog of the series we shall look at the usage of DFDs (data flow diagrams) as a starting point for threat modelling.
By Alastair Walker, Consultant & Owner
If you would like to join one of our cybersecurity training courses, take a look at our training courses for safety-relevant standards or if you are looking for consultancy support, please do not hesitate to contact us at info@lorit-consultancy.com.